 In recent months, rightsholders of all ilks have filed lawsuits against companies that develop AI models.
In recent months, rightsholders of all ilks have filed lawsuits against companies that develop AI models.
The list includes record labels, individual authors, visual artists, and more recently the New York Times. These rightsholders all object to the presumed use of their work without proper compensation.
A few hours ago, OpenAI responded to The New York Times complaint, asking the federal court to dismiss several key claims. Not just that, the defendants fire back with some rather damning allegations of their own.
OpenAI's motion directly challenges the Times's journalistic values, putting the company's truthfulness in doubt. The notion that ChatGPT can be used as a substitute for a newspaper subscription is overblown, they counter.
"In the real world, people do not use ChatGPT or any other OpenAI product for that purpose. Nor could they. In the ordinary course, one cannot use ChatGPT to serve up Times articles at will," the motion to dismiss reads.
'NYT Paid Someone to Hack OpenAI'?
In its complaint, the Times did show evidence that OpenAI's GPT-4 model was able to supposedly generate several paragraphs that matched content from its articles. However, that is not the full truth, OpenAI notes, suggesting that the newspaper crossed a line by hacking OpenAI products.
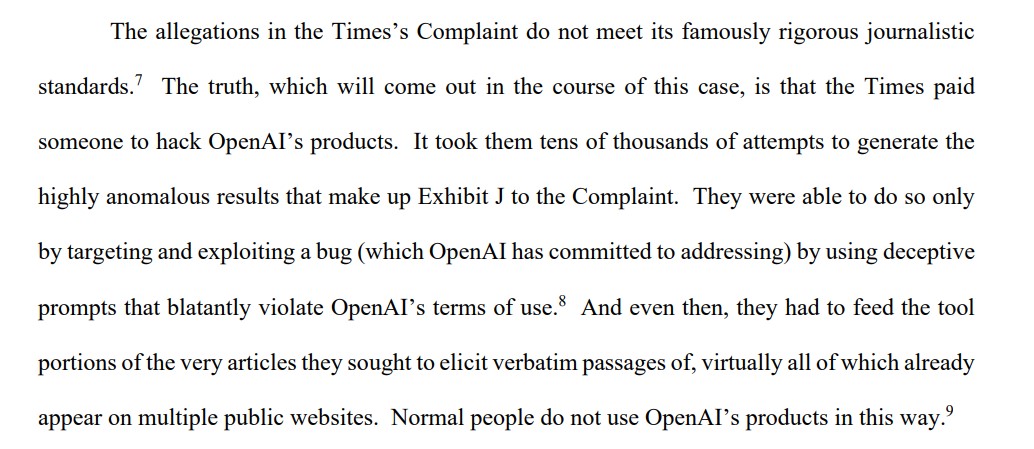
"The allegations in the Times's complaint do not meet its famously rigorous journalistic standards. The truth, which will come out in the course of this case, is that the Times paid someone to hack OpenAI's products," the motion to dismiss explains.
OpenAI believes that it took tens of thousands of attempts to get ChatGPT to produce the controversial output that's the basis of this lawsuit. This is not how normal people interact with its service, it notes.
It also shared some additional details on how this alleged 'hack' was carried out by this third-party.
"They were able to do so only by targeting and exploiting a bug […] by using deceptive prompts that blatantly violate OpenAI's terms of use. And even then, they had to feed the tool portions of the very articles they sought to elicit verbatim passages of, virtually all of which already appear on multiple public websites."
'Hired Guns Don't Stop Evolving Technology'
The OpenAI defendants continue their motion to dismiss by noting that AI is yet another technical evolution that will change the world, including journalism. It points out that several publishers openly support this progress.
For example, OpenAI has signed partnerships with other prominent news industry outlets including the Associated Press and Axel Springer. Smaller journalistic outlets are on board as well, and some plan to use AI-innovations to their benefit.
The Times doesn't have any agreements and uses this lawsuit to get proper compensation for the use of its work. However, OpenAI notes that the suggestion that its activities threaten journalism is overblown, or even fiction.
"The Times's suggestion that the contrived attacks of its hired gun show that the Fourth Estate is somehow imperiled by this technology is pure fiction. So too is its implication that the public en masse might mimic its agent's aberrant activity," the defense writes.
Fair Use
None of the allegations above address the copyright infringement allegations directly. However, OpenAI stresses that its use of third-party texts should fall under fair use. That applies to this case, and also to many other AI-related lawsuits, it argues.
This fair use defense has yet to be tested in court and will in great part determine the future of OpenAI and other AI technologies going forward.
To make its point, OpenAI aptly compares its use of third-party works in the journalistic realm. Newspapers, for example, are allowed to report on stories that are investigated and first reported by other journalists, as the Times regularly does.
"Established copyright doctrine will dictate that the Times cannot prevent AI models from acquiring knowledge about facts, any more than another news organization can prevent the Times itself from re-reporting stories it had no role in investigating," OpenAI writes.
The fair use defense will eventually be argued in detail when the case is heard on its merits. With the current motion to dismiss, OpenAI merely aims to limit the scope of the case.
Among other things, the defense argues that several of the copyright allegations are time-barred. In addition, the DMCA claim, the misappropriation claim, and the contributory infringement claim either fail or fall short.
—
Note: An earlier version of the article mistakenly mentioned Microsoft in relation to this motion. While the company is a defendant together with OpenAI, it is NOT part of this motion to dismiss.
A copy of OpenAI's motion to dismiss is available here (pdf). TorrentFreak broke this story, but other journalists are welcome to use it. A link would be much appreciated, of course, but we won't sue anyone over it
TorrentFreak asked the Times for a response to the 'hack' allegations but the company didn't immediately respond.
From: TF, for the latest news on copyright battles, piracy and more.
No comments:
Post a Comment