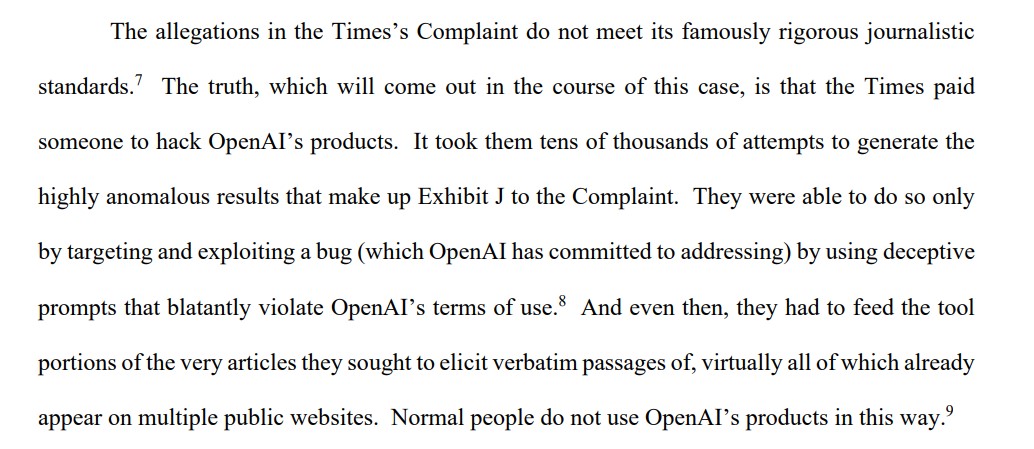
It's not uncommon for people to wander into some corner of the overall emulation scene with a specific question: Are emulators legal?
It's not uncommon for people to wander into some corner of the overall emulation scene with a specific question: Are emulators legal?
While not necessarily true, the most common answer is: yes, emulators are completely legal but distributing the games (ROMs) is most definitely not, so don't request them here.
In response to questions from those interested in the DIY approach, gamers are often advised to rip only the games they actually own, or only download games they intend to rip, for which they already own the original.
The endless caveats that tend to go unmentioned are even more important. Nintendo knows them all but rarely strays from its fundamental position that, as far as its games and consoles are concerned, the process is illegal.
Nintendo Targets Company Behind Switch Emulator, Yuzu
Targeting developers who reverse-engineer and decompile code, to support an open source project, for which no money needs to be paid, is one way to view the lawsuit Nintendo filed this week. At the heart of the complaint is Switch emulator software Yuzu and Tropic Haze LLC, the United States company allegedly behind the project.

Available on Windows, Linux, and Android, Yuzu claims to be the most popular open-source Switch emulator in the world. The software is completely free and readily available (caveats apply), but the games it plays are not part of the offer (see above).
Instead, users of Yuzu need to obtain Nintendo games from elsewhere, in most cases those pre-ripped by others and placed online for download.
In all cases, whether on physical cartridges or supplied as digital downloads, Switch games contain security measures designed to prevent copying or being run on unauthorized devices. Technological protection measures (TPM) are also present in the Switch console, which has layers of encryption to restrict access to vital cryptographic files known as 'prod.keys'.
Circumvention and Decryption
Just as Yuzu distances itself from pirated copies of Nintendo's games, Yuzu users must also independently obtain prod.keys, sourced from hacked Switch consoles and made available online.
After these keys are fed into Yuzu, Nintendo claims that the emulator uses them to unlawfully circumvent its technological measures, decrypting Switch game files before and during runtime. This allows copies of Switch games to be played on Windows, Linux, and Android, contrary to Nintendo's terms and conditions and in violation of the anti-circumvention provisions of the DMCA.

"Only because Yuzu decrypts a Nintendo Switch game file dynamically during operation can the game be played in Yuzu. In other words, without Yuzu's decryption of Nintendo's encryption, unauthorized copies of games could not be played on PCs or Android devices," the complaint reads.
"With Yuzu in hand, nothing stops a user from obtaining and playing unlawful copies of virtually any game made for the Nintendo Switch, all without paying a dime to Nintendo or to any of the hundreds of other game developers and publishers making and selling games for the Nintendo Switch. In effect, Yuzu turns general computing devices into tools for massive intellectual property infringement of Nintendo and others' copyrighted works."
Tropic Haze LLC and Yuzu Lead Dev, Bunnei
Tropic Haze LLC is described as a Rhode Island company that develops and distributes Yuzu. Nintendo says the company uses a network of paid coders/developers who maintain the software and issue updates to improve the software's ability to replicate the gameplay experience offered by Nintendo's official products.
These individuals are described as agents of Tropic Haze LLC and Nintendo holds the company liable for their conduct. That includes Bunnei, the alleged lead developer of Yuzu, whose conduct receives significant attention in the complaint.
Nintendo's Laundry List of Allegations
Nintendo's first mention of Bunnei includes a claim that the developer "publicly acknowledged most users pirate prod.keys and games online" while the Yuzu website offers instructions to users on how to "unlawfully hack their own Nintendo Switch and how to make unauthorized copies of Nintendo games and unlawfully obtain prod.keys."
While advice doesn't amount to circumvention, Nintendo says it can show that Bunnei and other developers used Yuzu to decrypt and play Nintendo games. That required them to obtain prod.keys from a hacked console (circumvention violation under the DMCA), and make at least one unauthorized copy of a game (copyright infringement).
Nintendo says that agents including Bunnei are "fully aware" of the use of Yuzu by others "in performing circumvention, and in facilitating piracy at a colossal scale." Moreover, in addition to providing Yuzu and instructions to complete various tasks, the importance of decryption keys is acknowledged on the Yuzu website, along with links to various pieces of software designed to extract those keys.
Nintendo claims that decisions regarding new Yuzu features, which platforms to launch on, and which games to provide compatibility with, are made by Bunnei. Nintendo also provides a quote; when acknowledging that the Yuzu Quickstart guide can be confusing, Bunnei allegedly said, "users probably just pirate a yuzu folder with everything."
The Quickstart guide itself also contains the following: "[t]o start playing commercial games, yuzu needs a couple of system files from a HACKABLE Nintendo Switch console in order to play them properly."
Zelda: TotK Leak Provided Patreon Earnings Boost
The Legend of Zelda: Tears of the Kingdom was released by Nintendo on March 12, 2023, but was available to pirate online on May 1, 2023. Nintendo says 100% of the copies available were necessarily pirated copies and every user who obtained a copy did so without paying for the game.
Over one million copies of the game were downloaded and Nintendo claims that over 20% of download links referenced playing the game on an emulator, Yuzu included. Meanwhile, Yuzu's Patreon – where early builds of Yuzu are made available to members – had a sudden increase in membership.

Nintendo claims this was a direct result of the leaked Zelda: TotK being played on Yuzu and Bunnei understood that, not least since Yuzu has a telemetry feature that relays the titles of games being played.
"Indeed, Bunnei implemented a ban on discussing Zelda: TotK emulation in Yuzu's Discord server because so many Yuzu users were trying to seek support emulating it," Nintendo claims.
Nintendo notes that 7,000 patrons now generate around $30,000 per month for those who develop Yuzu, with early versions accessible via Patreon generating an additional $50,000.
Nintendo's Claims
Nintendo's claims are comprehensive. Trafficking in circumvention technology in violation of 17 U.S.C. § 1201(a)(2)) is supported by allegations that the defendant and its agents are aware that Yuzu is designed, implemented and used to circumvent encryption, while they market Yuzu for the purpose of circumventing TPMs.
A claim of trafficking in circumvention technology in violation of 17 U.S.C. § 1201(b)(1)), notes that Yuzu has "only limited commercially significant purpose or use" other than to circumvent protection measures.
Circumvention of technological measures in violation of 17 U.S.C. § 1201(a)(1)) relates to Bunnei and other developers circumventing Nintendo's protection measures themselves, while additional claims under the Copyright Act relate to Bunnei and the other developers dumping Nintendo games, copying them into Yuzu, and sending them to each other.
A final count alleging contributory and inducement of infringement relate to secondary liability for Yuzu users' alleged infringements. Overall, the complaint amounts to a comprehensive sweep against almost everything that the modern emulation scene relies on, without directly tearing out the beating heart of emulation itself. If successful, the truck loads of banana peels left behind could prove difficult for other projects to avoid, however.
Nintendo seeks significant damages and an injunction to restrain Tropic Haze LLC from infringing its rights moving forward. That raises a slightly puzzling matter evident throughout the entire complaint.
Nobody Positively Identified in the Complaint
Despite Bunnei's alleged importance, the only defendant listed in the complaint is Tropic Haze LLC and Nintendo provides almost no information about the company, including details of ownership or control, despite claiming that its sole business is to "develop and distribute unlawful circumvention software."
It necessarily follows that 'Bunnei' is not listed as a defendant, Doe or otherwise. In fact, the language used by Nintendo throughout the complaint suggests that it either has no idea of Bunnei's true identity or may have gone to considerable lengths to give that impression.
What lies behind this, if anything, is unclear, but there's a strong possibility that sooner or later, pressure to settle will likely enter the equation. Right now, there are no real names in the complaint, but that could be changed in an instant, at least if any are currently known.
Nintendo's complaint can be found here (pdf)
From: TF, for the latest news on copyright battles, piracy and more.








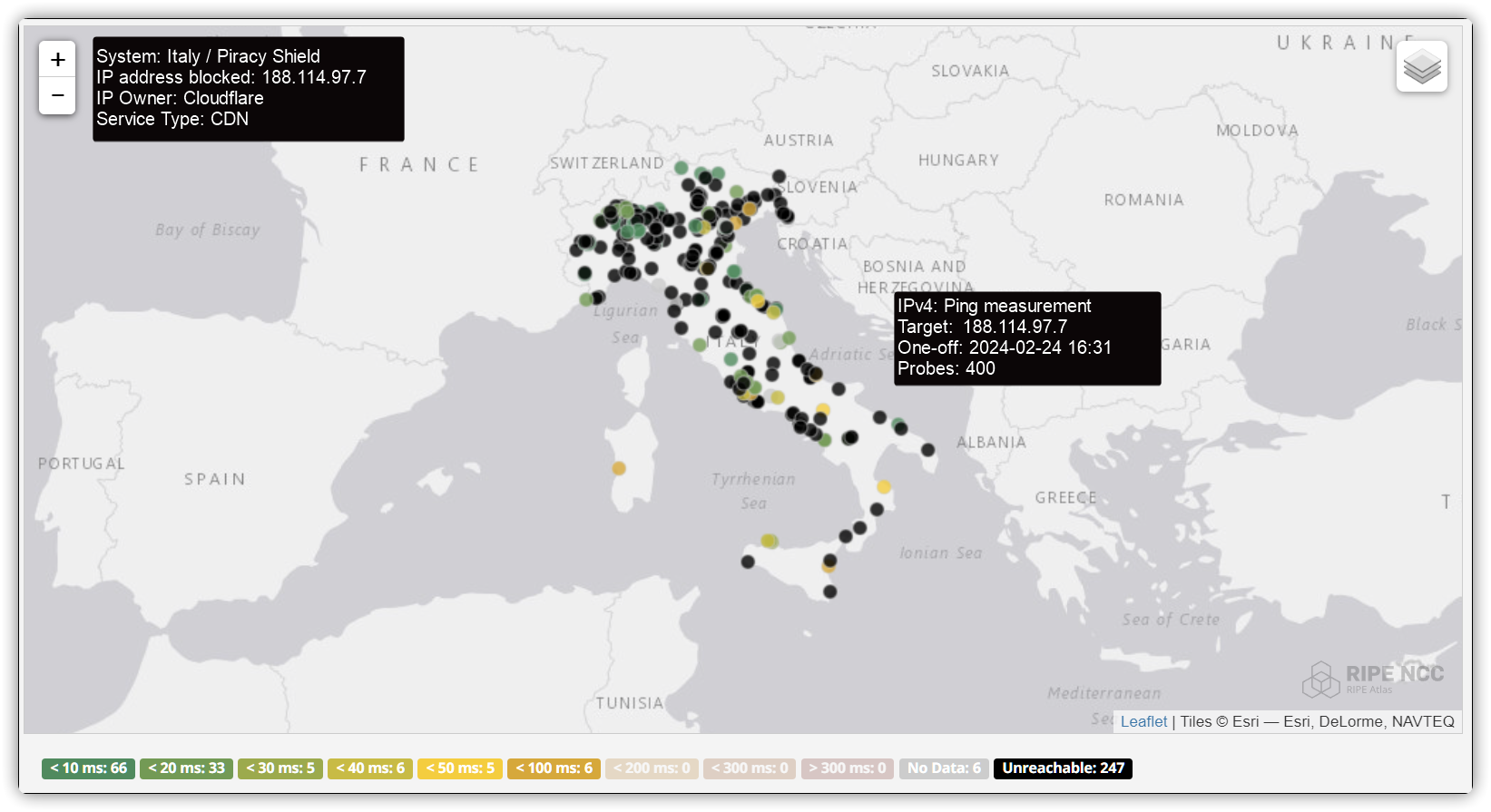
 Over the years, plenty of TV show episodes have leaked online in advance of their official release.
Over the years, plenty of TV show episodes have leaked online in advance of their official release. 

 In recent months, rightsholders of all ilks have
In recent months, rightsholders of all ilks have